
Cyber threats to energy infrastructure pose existential risks to businesses and critical systems alike. With ransomware and state-sponsored cyberattacks on the rise in 2025, decentralized grids and a digitized backbone create a growing web of complex vulnerabilities. Demonstratively, the number of susceptible points to cyber-energy attacks in U.S. electrical networks increases by ~60 per day. If unmitigated, these will disrupt operations and attract regulatory and investor scrutiny. Corporate boards are advised to integrate cyber-energy risks into enterprise risk frameworks, ensure third-party oversight, evaluate supply chain vulnerabilities, establish clear incident escalation protocols, and enhance operational resilience.
Key takeaways:
- Cyber-energy risks are existential, not theoretical. Large multinationals are only as resilient as their energy systems and are federally required to report material cyber incidents
- As grids grow more decentralized and digitized, the complex failure points multiply and pose systemic risk
- The grid’s virtual and physical weak spots, or points in software or hardware that are susceptible to cyber criminals, grew to a range of 23,000-24,000 in 2023 (up from 21,000-22,000 in the previous year)
- Operational and energy-related disruptions raise scrutiny from regulators, investors, and the public. Some 3% of cyber-energy attacks led to outages and other operational problems
What are cyber-energy attacks?
Cyber-energy attacks can target specific businesses as well as the energy sector more broadly, including power grids, oil and gas pipelines, and other critical infrastructure. These attacks, often motivated by financial gain, espionage, or geopolitical aims, can disrupt operations, cause significant financial losses, or even pose threats to public safety. Ransomware targeting industrial organizations has risen sharply through 2024 and into 2025, while state-sponsored groups have been found pre-positioning in U.S. critical infrastructure to enable potential disruption.
Exhibit 1. Utility company cyberattacks
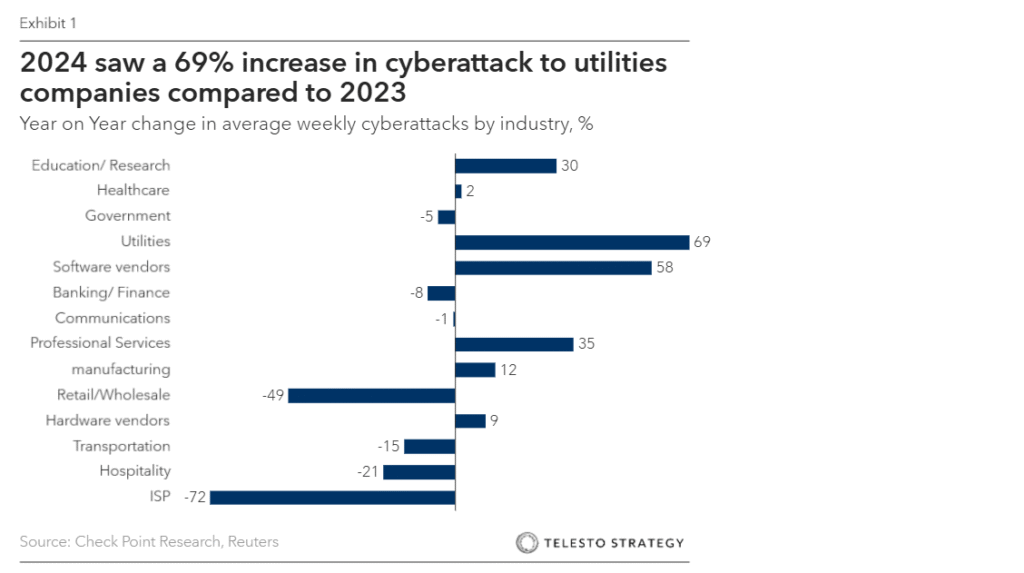
Exhibit 2. Espionage motivating factor to cyberattacks
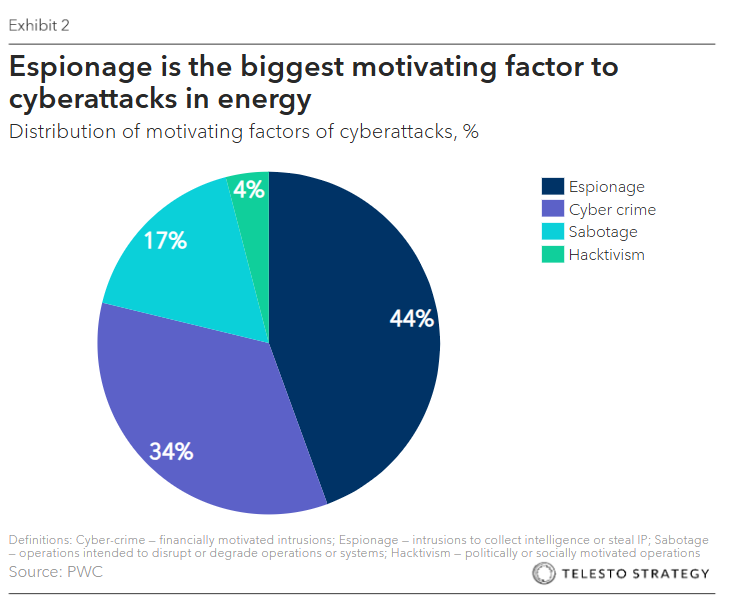
In what ways is the electricity grid vulnerable, and what could the impacts be if it were attacked? What are its potential weaknesses?
- Three interconnected transmission grids. The U.S. electricity grid is comprised of three interconnected transmission grids covering the contiguous U.S. ((i) western states, (ii) Texas, and (iii) the eastern U.S. and Midwest), as well as parts of Canada and Mexico
- Points of vulnerability. Grid distribution systems, which carry electricity from transmission systems to consumers, have grown more vulnerable, in part due to their operational technology increasingly allows remote access and connection to business networks
- Geopolitical threats. The U.S. grid has been more frequently targeted by adversarial countries, most commonly from China and Russia. Moreover, geopolitical conflict, including Russia’s invasion of Ukraine and the war in Gaza, have dramatically increased the number of cyber threats.
Exhibit 3. The U.S. Electricity Grid
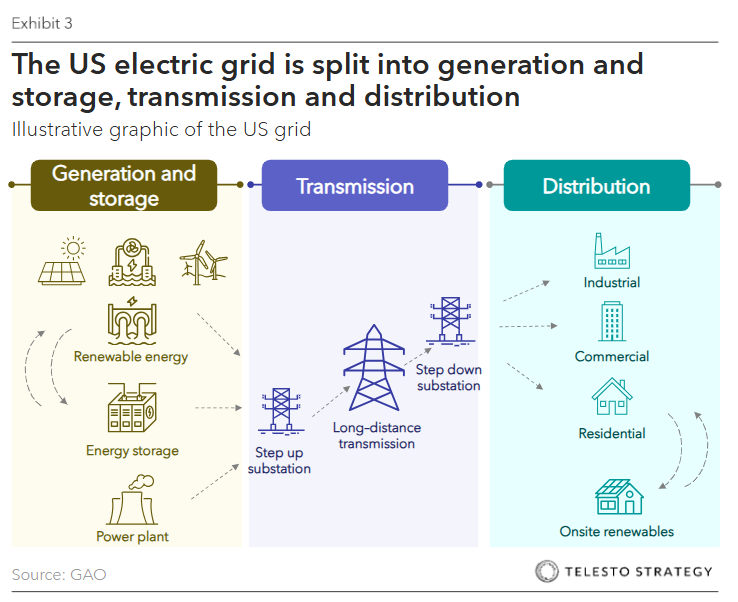
Exhibit 4. Example of an Attacker Compromising High-Wattage Networked Consumer Devices
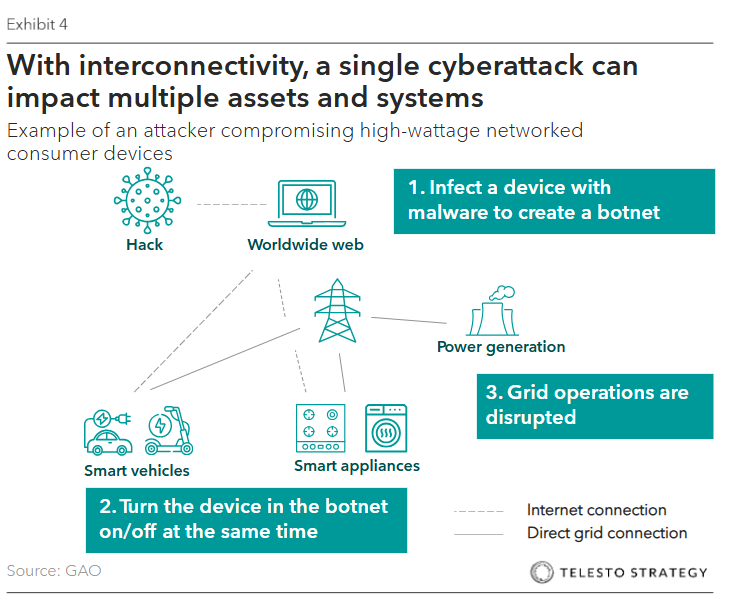
Federal measures to protect the grid
The U.S. has been implementing a cybersecurity strategy for protecting the grid and other federal departments, agencies, and infrastructure. In 2025, federal strategy emphasizes mandatory standards, incident reporting, public-private monitoring, and crisis response authorities. While progress is evident, risk remains elevated, especially at the distribution level. Core government strategies include:
- Mandatory Reliability Standards (NERC CIP). The Federal Energy Regulatory Commission (FERC) enforces cyber standards across the bulk power system. In July 2025, FERC approved CIP-015-1 (Internal Network Security Monitoring), requiring utilities to monitor traffic inside control networks—a significant uplift in visibility ad defense
- Supply Chain Risk Controls. Utilities must manage cyber risks from vendors and equipment providers under enhanced NERC CIP rules
- National Security Memorandum-22 (NSM-22). Designates the Cybersecurity and Infrastructure Security Agency (CISA) as the national coordinator for critical infrastructure security, requiring minimum cyber baselines across sectors
- Emergency Authority. Under FAST Act, the Department of Energy (DOE) can issue emergency orders to protect the grid during a cyber or physical “grid security emergency”
How is this impacting high-investment projects and businesses?
The energy system is now at the front line for both criminal and state-linked actors. Most incidents cause short-lived service interruptions or business process disruptions, but a handful have produced regional outages and credible safety risks.
- Colonial Pipeline. This ransomware attack forced a 5,500-mile refined products pipeline offline for six days, which triggered fuel shortages across the U.S. Southeast and emergency regulatory measures. Colonial paid a $4.4M ransom; the Department of Justice (DOJ) recovered $2.3M of the ransom
- Canada retail fuels. Suncor Energy experienced a cyberattack that disrupted Petro-Canada’s payment and loyalty systems, which left stations temporarily cash-only and affected supplier payments
- Norwegian hydropower dam. Pro-Russian hackers remotely opened a valve for ~4 hours (500 liters/second), which altered flows. Police and security services publicly attributed the attack
- ENGlobal Corporation. Experienced a ransomware attack in November 2024 that disrupted its systems for ~6 weeks and limited its operations to essential functions. As it provides services to the energy industry and U.S. government, hackers may have been interested in disrupting infrastructure, infiltrating U.S. government systems and infrastructure
- PPL Electric Utilities. In a February 2025 disclosure, PPL Electric Utilities confirmed that basic customer data was exposed in a data breach involving a third-party vendor that was originally affected in June 2023. The data was eventually published online by a Russian ransomware group in December 2024; critical infrastructure, however, was not affected
Actions boards can take:
- Integrate energy-grid cyber risks into enterprise frameworks. Require that management quantify potential financial exposure and cascading impacts, including indirect losses
- Ensure dedicated expertise and board education. Engage cyber risk advisors and energy specialists, and offer regular board education on grid-specific vulnerabilities and threat actors
- Establish clear escalation triggers. Define when management must escalate energy-grid cyber incidents (e.g., signs of intrusion, power anomalies, system misconfigurations)
- Integrate operational resilience to power dependencies. Data centers, plants, and critical facilities should have realistic islanding and manual modes, tested generator and fuel contracts, and prioritized load-shedding playbooks
- Embed operational redundancies. Require management to design redundant energy supply strategies and establish time-to-recovery metrics for both IT and OT systems
- Require third-party assurance. Require energy suppliers and critical vendors to meet cybersecurity standards
Questions for the boardroom:
- What is our quantified cyber-energy risk exposure, including indirect and cascading impact scenarios?
- Which energy systems are mission-critical to our global operations? How are they segmented and protected?
- How have we leveraged the latest federal and sector-level threat assessments (DOE, DHS/CISA, FERC, NERC) and what are these assessments telling us about risks to the U.S. grid?
- Do we have real-time visibility into cyber intrusions at our energy-reliant sites worldwide? And those of our most important suppliers?
- How are we monitoring compliance with evolving U.S. and EU regulations?
- Who at the management level owns energy-related cyber-risk, and how does it tie to CFO, CSO, and CIO responsibilities?
- How have we integrated cyber-energy scenarios into both the ERM and insurance coverage assessments?
Additional Telesto resources:
- Navigating shifting political risk under Trump 2.0 – how companies are staying ahead
- Atlas equips your organization’s corporate directors and leaders with the insights and knowledge necessary to stay up to date, mitigate risks, and seize business opportunities associated with sustainability, climate, and ESG
- Odyssey is a fully customizable, AI- and Machine Learning-driven platform which allows your organization to generate operating cost savings and improve capex planning in your sustainability journey.
- Recently released by Telesto Strategy’s CEO & Founder, Alex Kruzel, The Courage to Continue: Stay the Course on Sustainability to Secure our Future, explores the connection between corporate priorities and President Trump’s national security agenda




