
Copyright © 2025 Telesto Strategy, LLC
All rights reserved
Key takeaways
What are cyber-energy attacks?
Cyber-energy attacks target both companies and the broader energy system – grids, pipelines, and critical infrastructure. Motivations range from financial extortion to espionage and geopolitical disruption. Ransomware aimed at industrial organizations surged through 2024 and 2025, while state-backed actors are embedding themselves in U.S. critical infrastructure to enable future disruption.
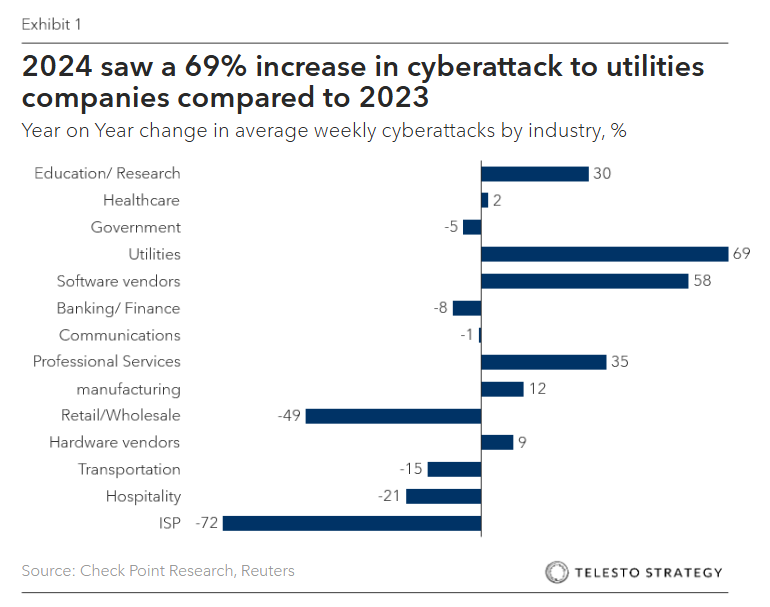
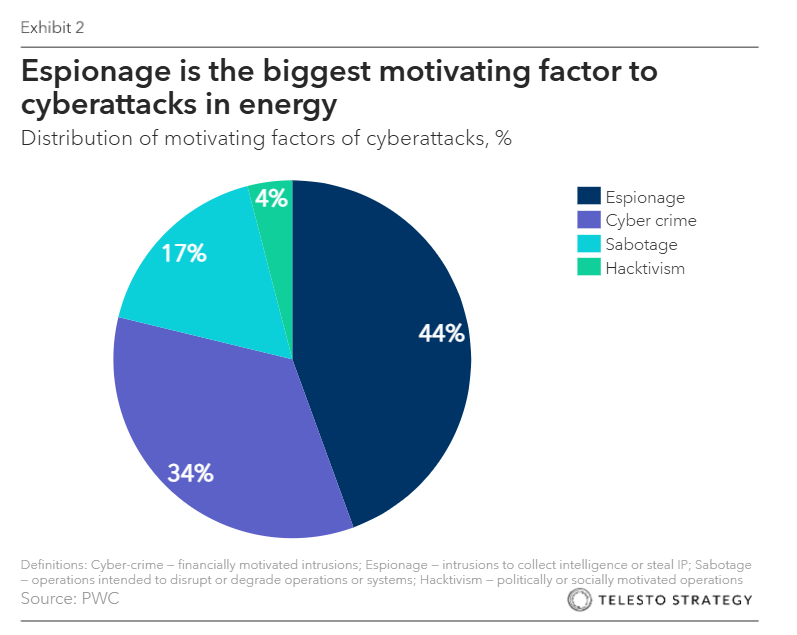
How is the electricity grid vulnerable?
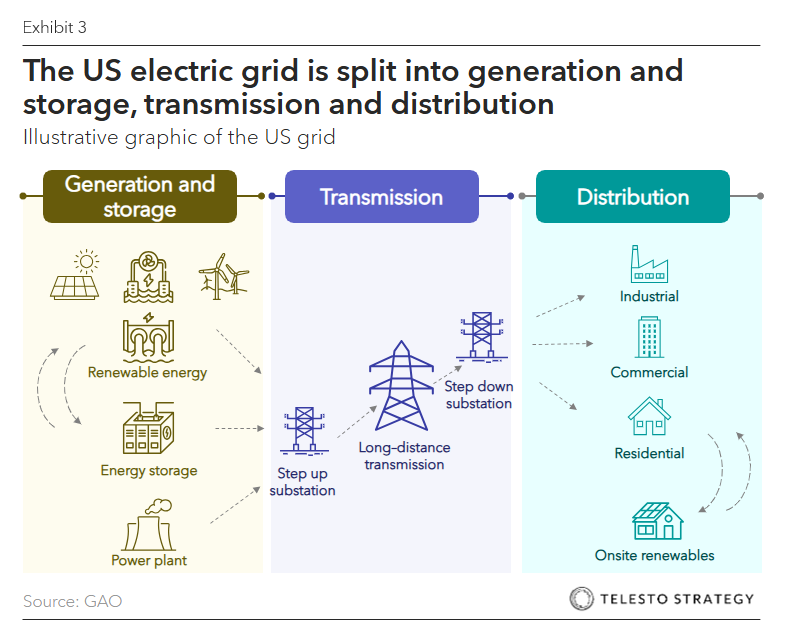
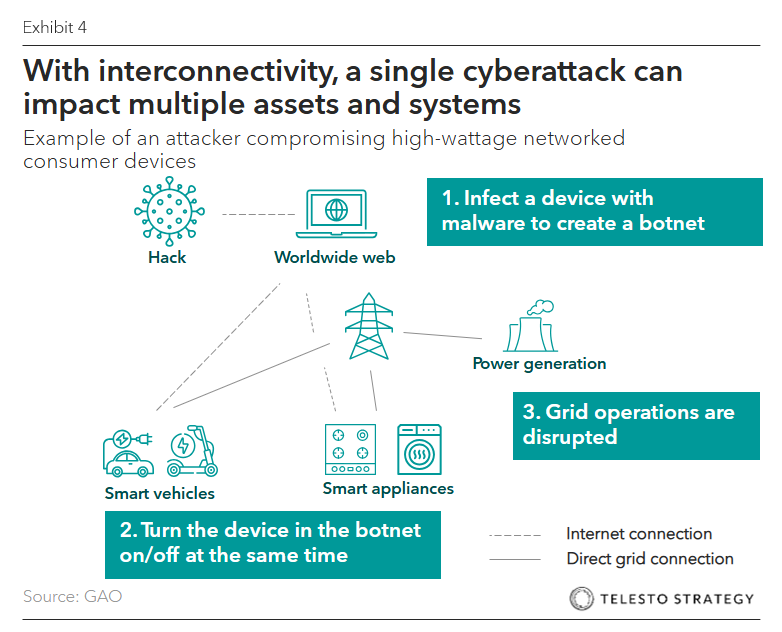
Federal response measures
The U.S. has rolled out stronger cybersecurity protections for the grid, but risk remains high, especially in distribution systems. Recent steps include:
Business and project impact
Cyber-energy threats are hitting high-investment projects and everyday business operations:
Actions management teams should take
Executive questions to address
Additional Telesto resources
Partner with Telesto to assess your company’s exposure, harden your most critical operations, and build resilience into the systems your business cannot afford to lose.

Copyright © 2025 Telesto Strategy, LLC
All rights reserved